Signing Manager
Take Control of Your Signing Certificates
Signing Manager provides an ideal system for securing code and package signing certificates. Implement secure access to the signing operations with API keys, access controls, and auditing. Gain full control over iOS, macOS, watchOS, and iPadOS app signing without disrupting the current workflow. Signing Manager works great for developers, CI/CD servers, or for any size team that releases software on Apple hardware.
Free Install Pricing Buy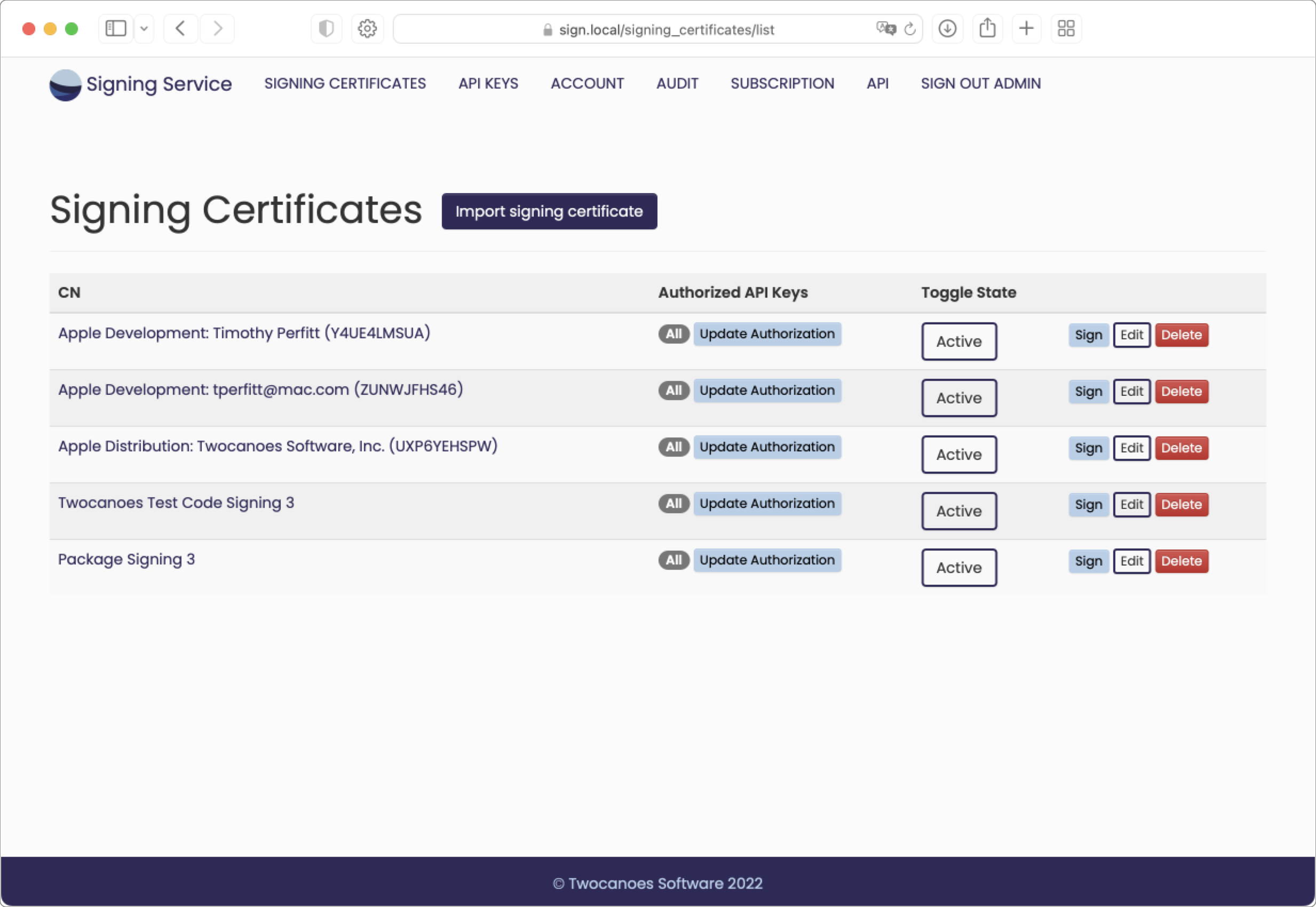
Try Secure Remote Access for 14 Days!
Fill out this form to download your 14-day trial. You will receive an email with links to download your software and trial license. If you have already requested a trial and would like additional time, please contact us.
See It In Action
- Free
- $0
- A Great Match for a Small Project
✓ One Signing Certificate
✓ 30 Signing Operations per Month
✓ 3 Day Logging and Auditing
✓ One API User / Machine
✓ HSM-backed credentials
✓ Forum and Slack Support
- Pro
- $3
- Per Device Per Month
✓ Up to 3 Signing Certificates
✓ 3000 Signing Operations per Month
✓ One Month Logging and Auditing
✓ HSM-backed credentials
✓ Three Day Phone, Email and Slack Support
- Enterprise
- $20
- Per Device Per Month
✓ Unlimited Signing Certificates
✓ Unlimited Signing Operations per Month
✓ One Year Logging and Auditing
✓ HSM-backed credentials
✓ Custom Login via Identity Provider
✓ Same Business Day via Phone, Email and Slack Support
macOS
- Sign apps and packages without direct access to private keys
- Sign iOS, iPadOS, tvOS, macOS apps
- Local signing with native Apple tools (codesign/productbuild/Xcode)
- Limit signing operations based on API key
- Full auditing of all signing operations
- Easy updating of expired certificates
- Command line interface for CI/CD servers
- Support for all build systems (Jenkins, Github, more)
Web
- Manage Signing Certificates
- Manage Client Machines
- Manage API Keys
- Manage Certificate Signing Permissions
- Auditing and Logging of Signing Operations
- Deploy on macOS, Linux, or Cloud using Docker or Kubernetes
- Google HSM Support (optional)
Secure
All the private keys associated with code signing or package signing certificates are not exposed to the process doing the signing. Only approved requests are allowed to perform signing operations, and an audit log is kept of all signing operations.

Easy To Use
The Signing Manager app just requires an API key and a URL. Once those values are configured, certificates are available for signing operations. The certificates are automatically added to the keychain and are shown in Signing Manager. Apple signing tools request the certificate based on a fingerprint or name of the certificate, and Signing Manager handles the rest.
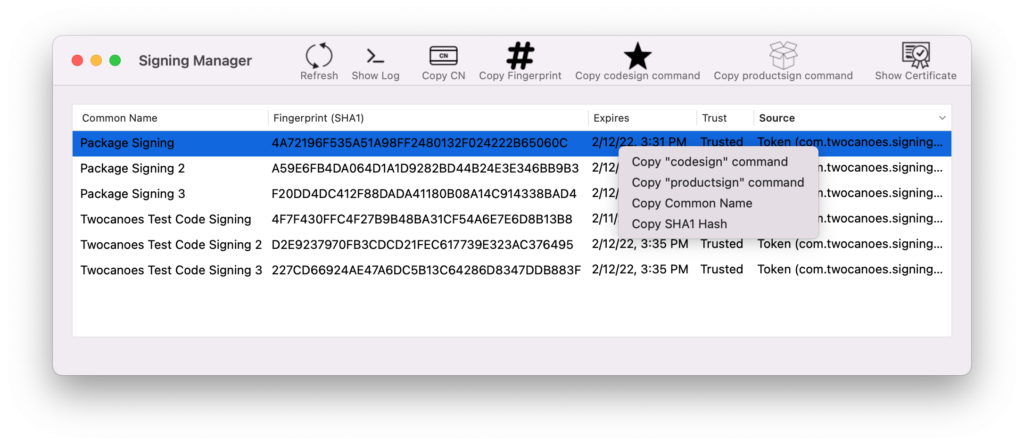
Use Built-in Signing Tools
Sign apps and packages using the built-in signing tools: codesign, xcodebuild, xcodearchive, productsign and more. All signing operations are transparent to the existing toolchain. All operations for configuring Signing Manager, discovering certificates, and signing binaries can be done on the command line, so it makes for an ideal solution for Developers using Xcode, Release Managers, or CI/CD Servers.

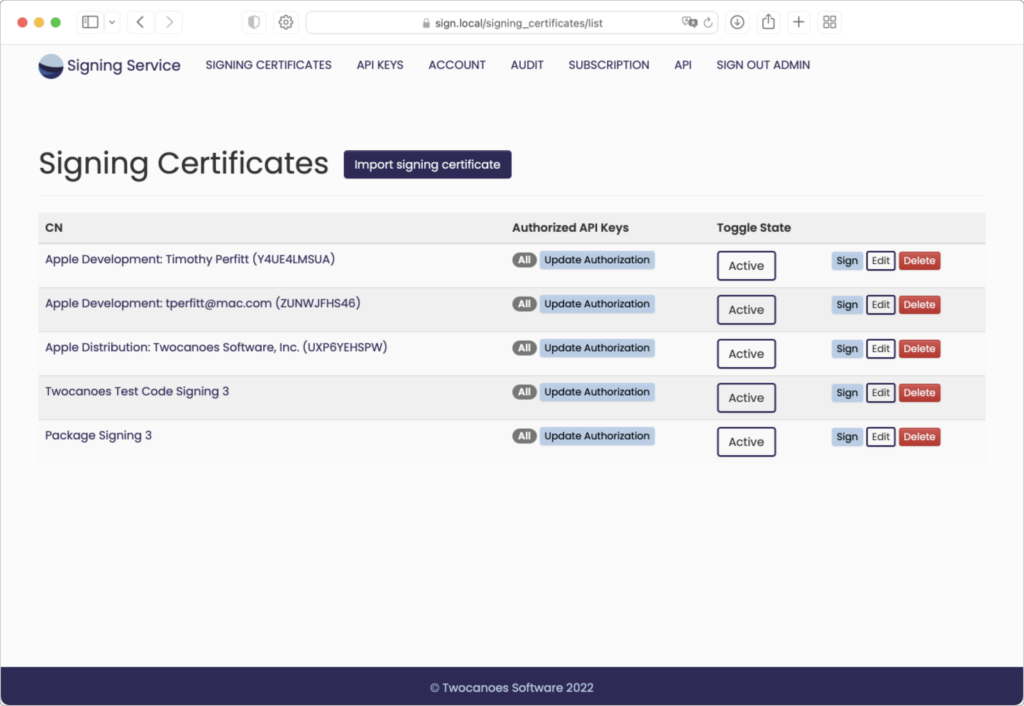
Import and Manage Signing Certificates
Import existing signing certificates into Signing Service from your macOS keychain and make them available for signing operations.
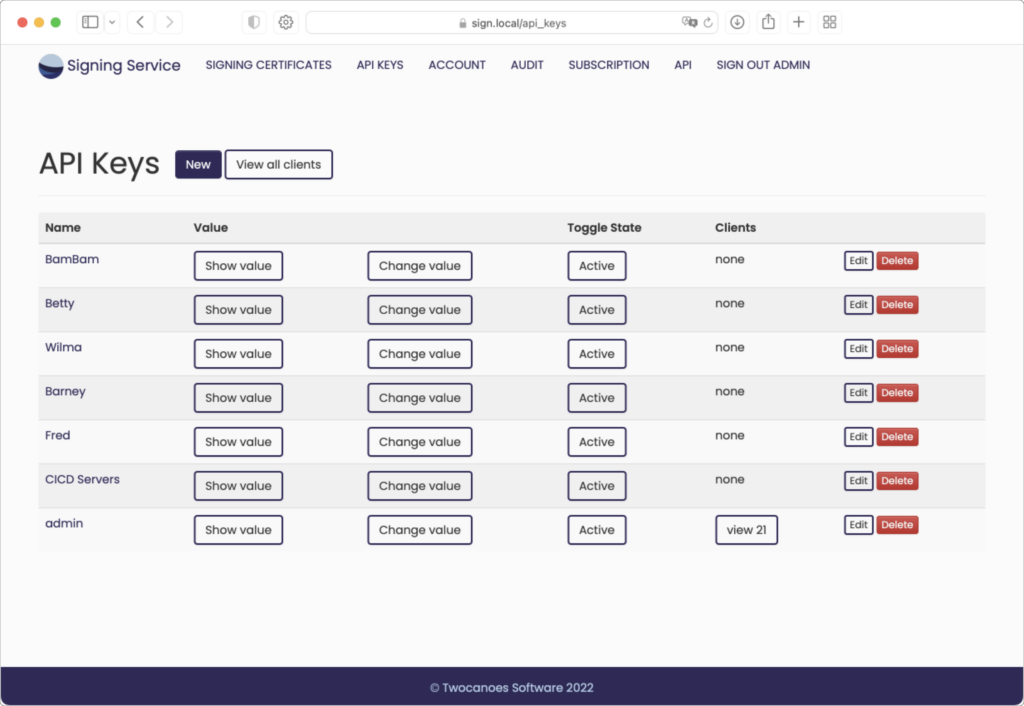
Generate API keys
Generate API keys to grant and limit access to signing operations on any of the imported signing certificates. Easily disable or revoke access to an API key to keep your signing certificates and signing operations secure.
Full Auditing
Every operation is logged in the audit log so you will know when a signing operation has been attempted. Export logs for offline analysis or long term storage.
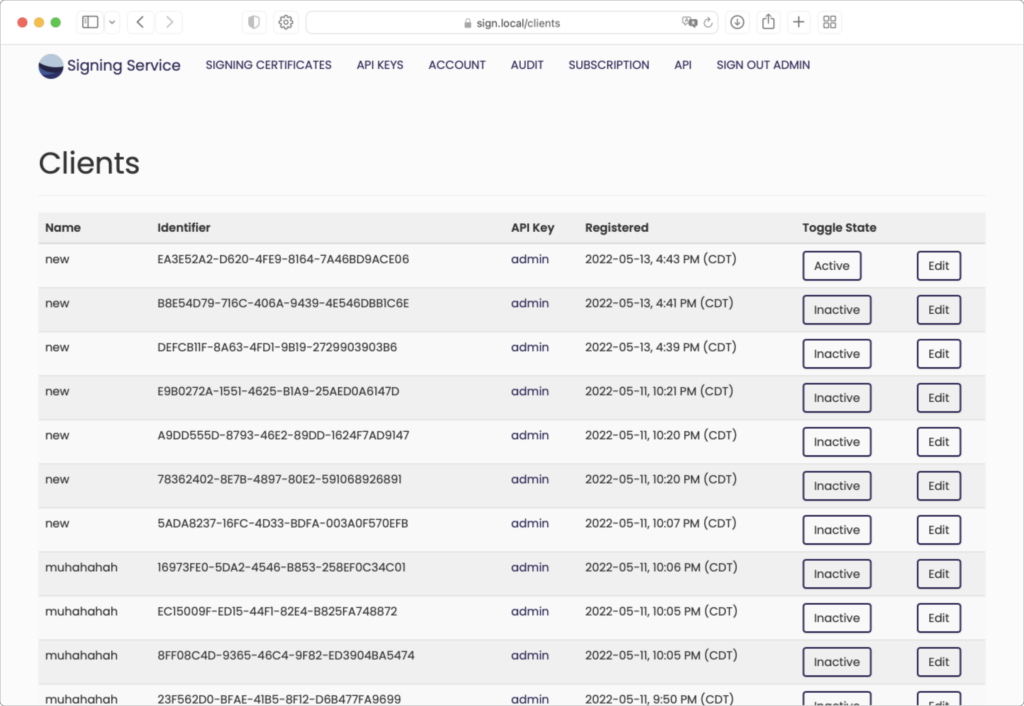
Manage Clients
Signing Service makes deployment easy! One API key can be shared to multiple clients in the same trusted boundary and the clients register themselves automatically. Clients are easily configured by macOS configuration profiles or through local preferences.
Resources
System Requirements
- Signing Manager: macOS 13 Ventura or 14 Sonoma
- Signing Service: macOS, Windows, or Linux capable of running Docker or Docker Desktop

