Troubleshooting Certificate Request
Certificate Request automatically queries Active Directory for relevant resources. If Certificate Request is failing to lookup the resources, you can try the following:
1. Verify that Certificate Request can find a domain controller by using a service record lookups in DNS:
host -t SRV _ldap._tcp.twocanoes.com
which returns:
_ldap._tcp.twocanoes.com has SRV record 0 100 389 WIN-FGIVT3J3GI9.twocanoes.com.
2. Verify that you have a Kerberos ticket:
klist
You should see Principal with your user and the domain. For instance:
Principal: tperfitt@TWOCANOES.COM
You should also see a krbtgt (your Kerberos ticket):
krbtgt/TWOCANOES.COM@TWOCANOES.COM
This is the ticket that is used for access to other services
3. Query for the Certificate Authority using ldapsearch:
ldapsearch -b “CN=Certification Authorities,CN=Public Key Services,CN=Services,cn=Configuration,dc=DOMAIN,dc=COM” -h SERVER.DOMAIN.COM “(objectclass=certificationAuthority)” “name”
Replace dc=DOMAIN, dc=COM with your domain components, and SERVER.DOMAIN.COM with the domain controller found in step 1. For example:
ldapsearch -b “CN=Certification Authorities,CN=Public Key Services,CN=Services,cn=Configuration,dc=twocanoes,dc=com” -h WIN-FGIVT3J3GI9.twocanoes.com “(objectclass=certificationAuthority)” “name”
Which returns:….
name: TCS CA
…
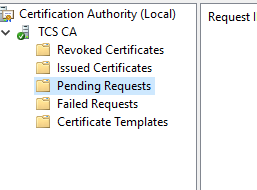
4. Request waiting approval
If you receive this message, it means that the template used in the Active Directory Certificate Authority requires approval from an administrator. The request is queued up in Certificate Authority:
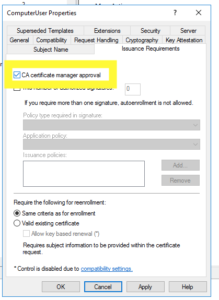
An administrator can change the template to not require operator intervention by deselecting this box in the template:
We are looking at adding the functionality to download approved certificates in a future release.