What’s New in XCreds 4.1
Customization of Menu
We added in the ability to customize the appearance and add new items to the XCreds menu item. The menu now shows the username for both Active Directory and OIDC logins, allows you to set a background image when prompting for password updates, and even allows you to add in your own menu items to open apps and websites.
Background Image
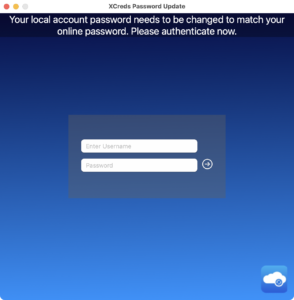
When prompting for a user’s Active Directory credentials, a new default background will be shown. This is customizable using the menuItemWindowBackgroundImageURL key and providing a string to a local file path or URL.
Adding Menu Items
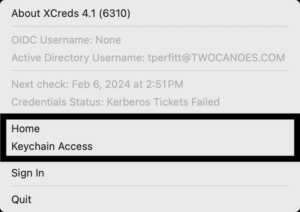
If you want to customize the XCreds menu item, you can now easily add items to local applications or to web URLs. You can also add in separators before or after the items:
There is a new menuItems key that defines an array of items (dictionary). The items define a linkOrAppPath that is either starts with “/” (app) or “http” (URL). The menuItemName key defines the name that will show in the menu, and two boolean keys define the separators: separatorBefore and separatorAfter. An example snippet is shown below.
<key>menuItems</key>
<array>
<dict>
<key>linkOrAppPath</key>
<string>https://twocanoes.com</string>
<key>menuItemName</key>
<string>Home</string>
<key>separatorAfter</key>
<false/>
<key>separatorBefore</key>
<true/>
</dict>
<dict>
<key>linkOrAppPath</key>
<string>/System/Applications/Utilities/Keychain Access.app</string>
<key>menuItemName</key>
<string>Keychain Access</string>
<key>separatorAfter</key>
<true/>
<key>separatorBefore</key>
<false/>
</dict>
</array>
Menu Username
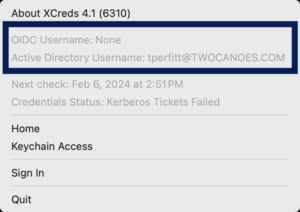
The XCreds menu now shows the OIDC username and Active Directory username so you know exactly what user account with which you are logged in.
Cloud + Active Directory
Admins started using both OIDC and Active Directory configurations at the same time. This adds some exciting opportunities, so XCreds 4.1 was updated to ensure that XCreds works appropriately when both Active Directory and OIDC are defined in the preferences. The new key mapKerberosPrincipalName specifies an OIDC claim with the user’s Kerberos principal name. If that claim is returned when logging in via OIDC and Active Directory has been configured in XCreds preferences, a Kerberos ticket will be obtained by using the Kerberos principal name and the cloud password. Once the Kerberos ticket is obtained, defined shares will then be mounted. This allows cloud users to take advantage of resources on their local network provided by Active Directory and SMB shares.
SMB Share Mounting
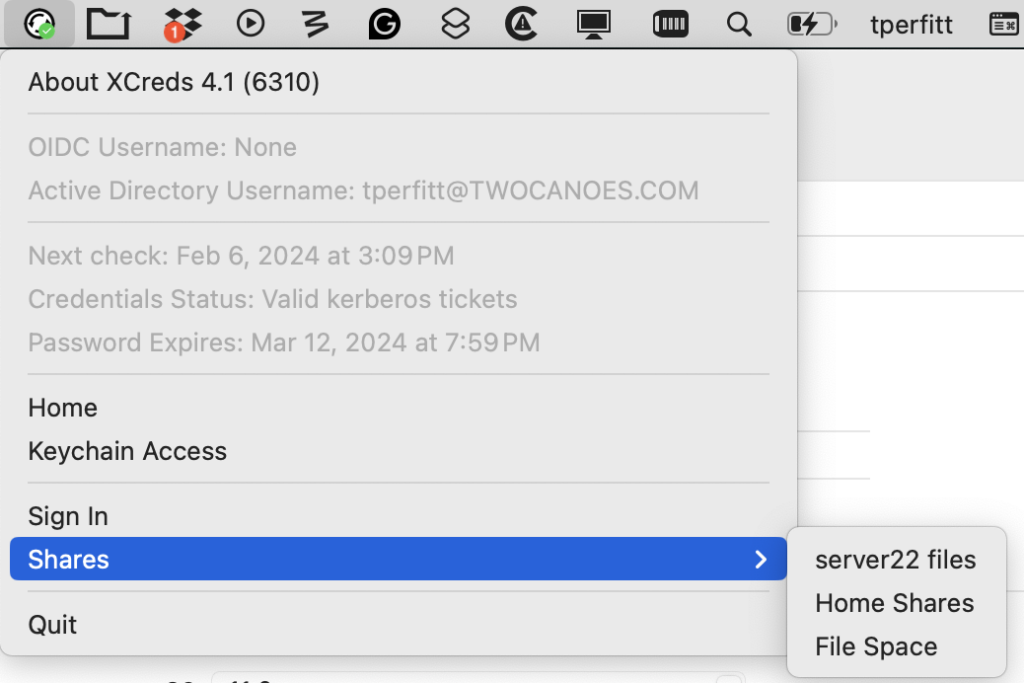
SMB shares can now be defined in the XCreds configurator profile. The configuration for group shares is the same format as NoMAD and the preferences for home directory mounting has changed slightly. Both are defined in the Profile Manifest:
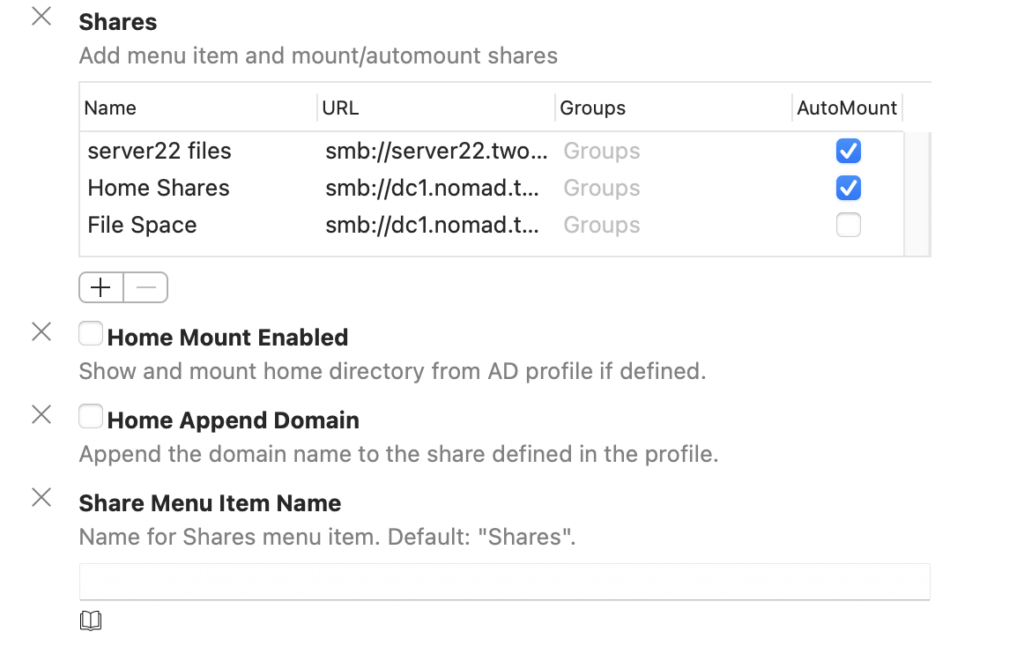
If Groups is left undefined, the share will be mounted for all AD users. If the name of an AD group is specified, only those users who are members will have the share mounted. Since the shares are available from the XCreds menu, the shares are mounted on demand or automatically when XCreds is first launched.
The following new keys are defined:
Shares: An array of shares (dictionary)Automount: Boolean. Set to true to automatically mount when XCreds startsGroups: Array of strings that specify AD groups. If the user is a member of the group, the share will be mounted.Name: String. This is what will show up as the title of the menu item.URL: String. the SMB share path.
Here is a sample Share definition:
<key>Shares</key>
<array>
<dict>
<key>AutoMount</key>
<true/>
<key>Groups</key>
<array>
<string>XCred Shares</string>
</array>
<key>Name</key>
<string>server22 files</string>
<key>URL</key>
<string>smb://server22.twocanoes.com/Files</string>
</dict>
<dict>
<key>AutoMount</key>
<true/>
<key>Groups</key>
<array/>
<key>Name</key>
<string>Home Shares</string>
<key>URL</key>
<string>smb://dc1.nomad.test/Homes</string>
</dict>
<dict>
<key>AutoMount</key>
<false/>
<key>Groups</key>
<array/>
<key>Name</key>
<string>File Space</string>
<key>URL</key>
<string>smb://dc1.nomad.test/File Space</string>
</dict>
</array>
Two additional keys have been defined: HomeAppendDomain and shareMenuItemName. The key HomeAppendDomain will add the domain name to the share path found in AD profile when normalizing. For example, if the domain is twocanoes.com and the home directory is defined as \\server\Homes\tperfitt, this will be changed to smb://server.twocanoes.com/Homes/tperfitt if HomeAppendDomain is set to true. The key shareMenuItemName lets you customize the name of the top level share menu item (by default it is Shares).
Admin Removal
In prior versions of XCreds, the key CreateAdminIfGroupMember allowed you to add group names into an array and if the user was a member of any of those groups, then the user would be created as an admin. In XCreds 4.0, we made the feature better by checking this at each login and promoting to admin if the user was added to any of those groups. In XCreds 4.1, we now track if XCreds added them to the admin group. Then if the user is later removed from the AD groups defined, XCreds will demote them to a standard user. XCreds will not demote the user account if it is the last admin.
All Changes
- fixed issue with menu item not updating tokens View
- fixed automount View
- remove admin if we made them admin View
- added check for not removing last admin user View
- fixed prompting when both AD and cloud are configured View
- added
mapKerberosPrincipalNamepref and getting kerb ticket with oidc login View - added
menuItemWindowBackgroundImageURLView - better selection of menu item prompting if both AD and OIDC is setup View
- fixed issue with ACL on tokens in keychain View
- added custom menu item pref View
- ability to customize Share menu item; added username for AD and OIDC in menu View
- added pref for shares View
- added better descriptions to share manifest View
- updated whats new View
- updated manifest View
