Wrapping Private Keys for Google HSM from macOS Keychain
We are integrating Hardware Security Module (HSM) support for our Signing Service!
Importing existing developer identities is important; Signing Service is a secure service for managing your Apple developer certificates and private keys. While using a .p12 file is very common way to export and share identities, it doesn’t work well for an HSM. The Google Cloud HSM requires that private keys be wrapped in a specific format. When the private key is encrypted with a password when uploaded to a service (like ours), it is extracted and imported into the HSM: this exposes the private key to the service.
To avoid this, the HSM requires the private key be encrypted with the HSM’s public key, so that only the HSM can decrypt it. Since the data to be encrypted is larger than an asymmetric key can encrypt, a symmetric key is generated to encrypt the private key. Then, the symmetric key is encrypted with the HSM public key. Read more information on this process here.
To make this easier for customers that have Apple Developer identities in an existing keychain, we created an app that prompts you to select identities from your keychain, provide the public key of the HSM, and save all the private keys—wrapped correctly and ready to be uploaded.
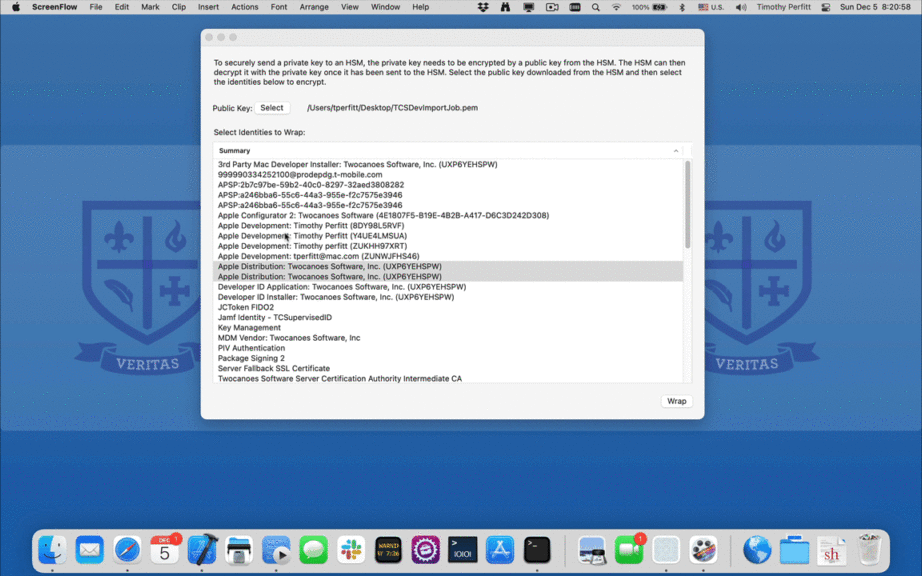
Once the wrapped keys are exported, they can be uploaded to our service or directly to the Google HSM:
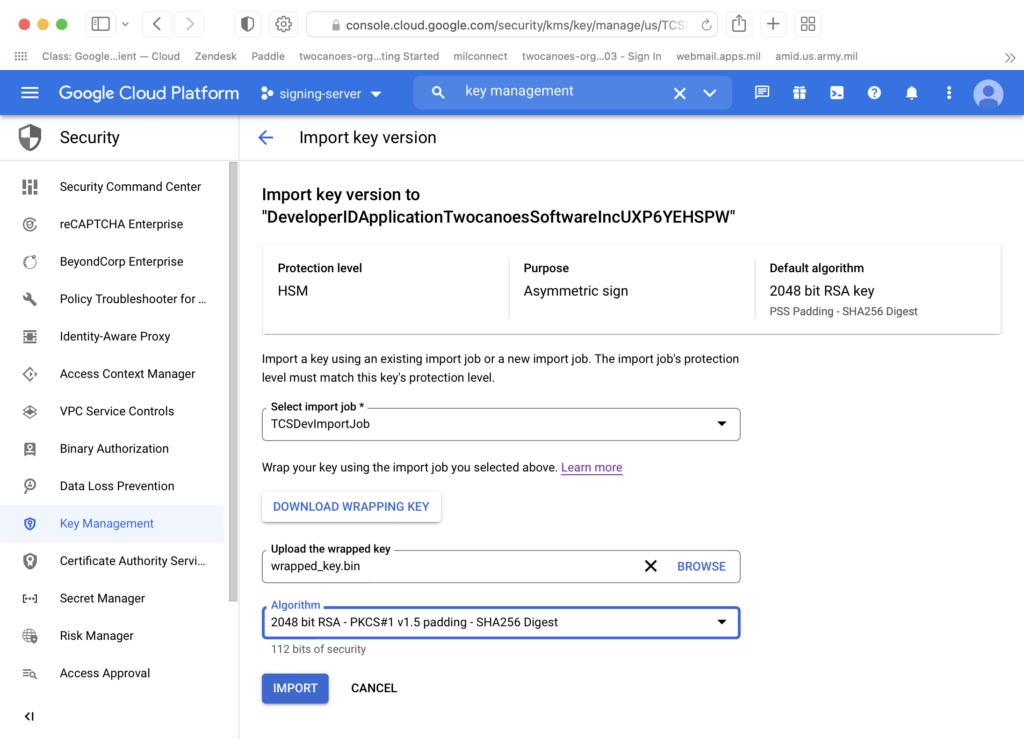
If you are interested in this tool or our Signing Service, get in touch!
