Using XCreds with Okta ROPG
Okta, along with some other Identity Providers, does not revoke refresh tokens on password changes. This prevents XCreds from successfully detecting password changes when using Okta since the current method of checking password validity is via refresh tokens. As an alternative, XCreds can now be configured to check password validity via Resource Owner Password flow aka ROPG.
Okta Setup Required
For this work, an additional app will need to be created in Okta as described in the ROPG flow docs.
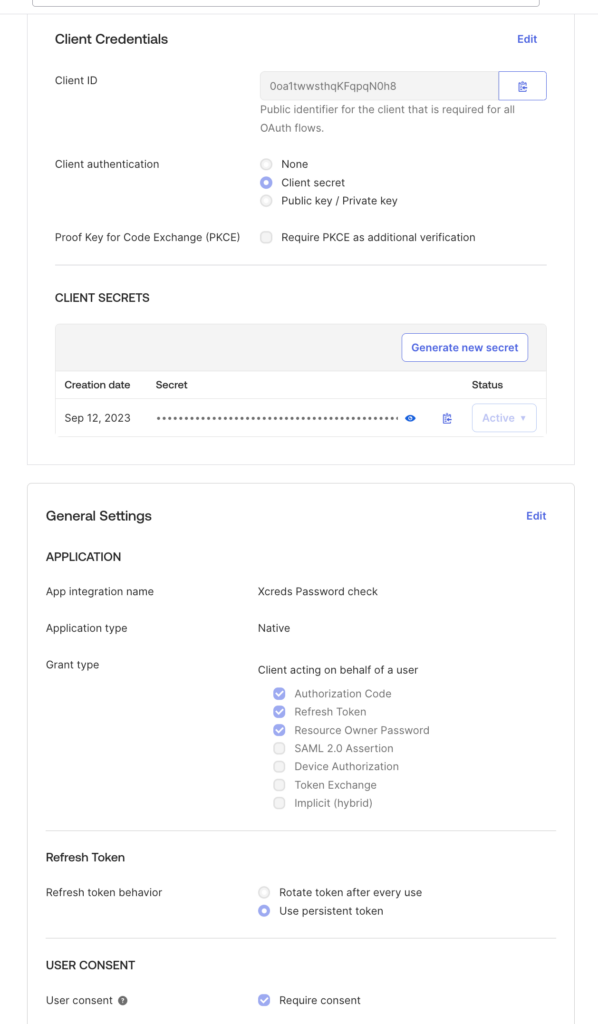
If a tenant is using OIE it might have to deploy a custom sign-in policy for the app that only enforces a single factor for authentication. This is a departure from how the classic engine works whereby it defaults to single factor challenge for ROPG flows.
These preference keys can be configured using Profile Creator as described in the XCreds admin guide.
If any of the keys above are missing XCreds will default to using refresh token flow for password verification.
There are additional preference keys that have been added to make this possible.
<key>shouldUseROPGForLoginWindowLogin</key>
<true/>
<key>shouldUseROPGForMenuLogin</key>
<false/>
<key>shouldUseROPGForPasswordChangeChecking</key>
<true/>The following optional preference keys may also be desired for use when configuring ROPG.
<key>shouldShowMacLoginButton</key>
<false/>
<key>shouldAllowKeyComboForMacLoginWindow</key>
<true/>DEPRECATED By XCreds 4.0
Prior to version 4.0 the following preference keys were used to configure ROPG.
<key>shouldVerifyPasswordWithRopg</key>
<true/>
<key>ropgClientID</key>
<string>appclientID</string>
<key>ropgClientSecret</key>
<string>oktaAppSecret</string>